Overview
CVE-2022-30190, known as Follina, was released by Microsoft on Monday, May 30th, 2022. The vulnerability resides within the Microsoft Support Diagnostics Tool (MSDT), which may allow an attacker to run arbitrary code with the privileges of the calling application. Microsoft Office applications use MSDT to troubleshoot and collect diagnostic information when something goes wrong.
This vulnerability was discovered by the independent cybersecurity researchers at nao_sec after they noticed a strange word document posted to VirusTotal. Using the Remote Template feature in Microsoft Word, an HTML file was pulled from a remote web server. It then made use of the “ms-msdt://” URI scheme to run a malicious payload. Experts are now saying this vulnerability is being exploited by attackers in the wild. Some security researchers have demonstrated execution of the malicious code merely by previewing the document in Windows File Explorer or Outlook.
Exploit
The video below demonstrates how easily this vulnerability can be exploited. Exploit code is now publicly available, making this process trivial. We will outline the steps taken in this video below:
- An attacker downloads exploit code from GitHub.
- This exploit code is then utilized to create the malicious Word document and stand up a web server to serve up the HTML file. In the video below, this Word document is called “sploit.docx.”
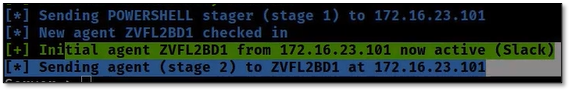
- Once the user opens the Word document, you see the MSDT tool also fire off. MSDT is also commonly referred to as “Program Compatibility Troubleshooter.”
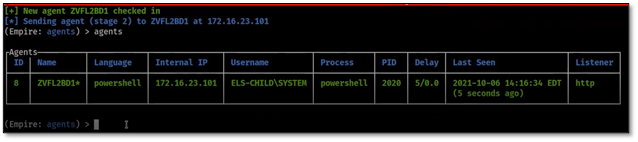
- The producer of this video then shows you that both a cmd.exe process and powershell.exe process have been launched on the system. At this point, the document can be closed, but the malicious process is still running.
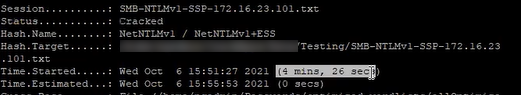
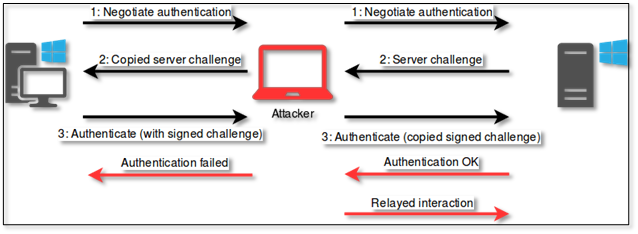
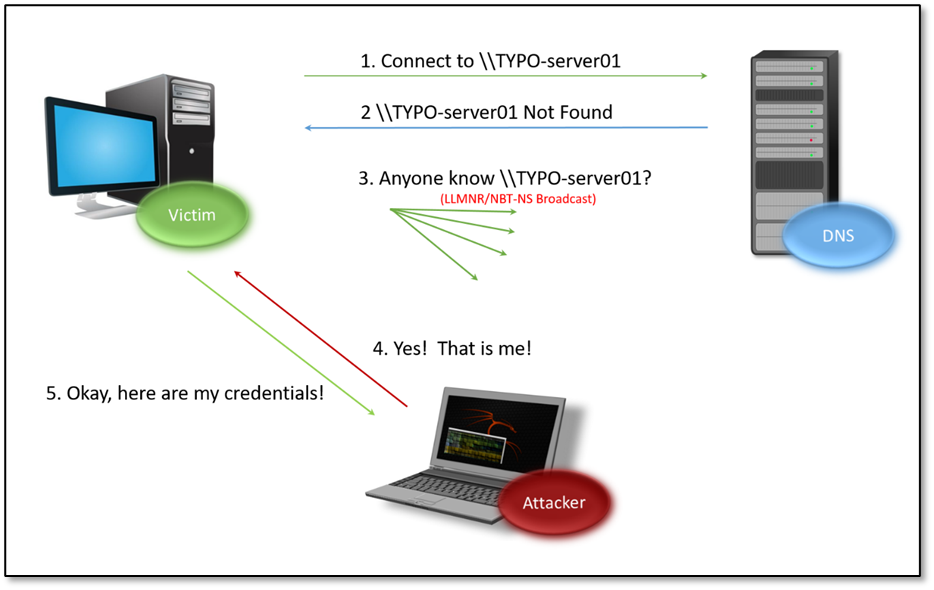
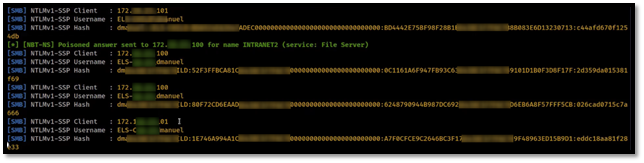
- The demo then shows a Cobalt Strike window. Cobalt Strike is a command-and-control framework used for maintaining persistent access on compromised systems. You can see in the video that a “beacon” has been launched on the system. A beacon is an agent on the system that allows an attacker to maintain persistent access and run arbitrary code.
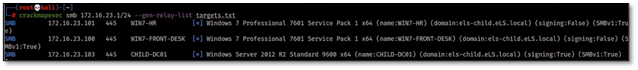
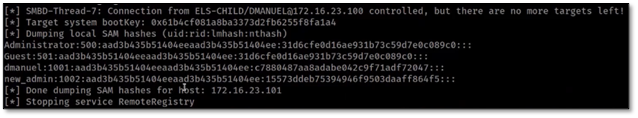
- At this point the producer of this video runs “whoami” on the system itself to show you which user account launched the Word document. They then flip back to Cobalt Strike and run “whoami” from the interactive beacon. This displays the same user account. Persistent remote code execution achieved.
What To Do?
At this point in time, Microsoft has not released an official fix for this vulnerability. They are recommending that the MSDT URL protocol be disabled in order to protect systems from this vulnerability. That guidance can be found here. nGuard offers a bevy of services that can help prevent and identify these types of attacks. Both Social Engineering simulations and Social Engineering Awareness Training can assist your organizations employees in identifying these types of attacks. Internal Penetration Testing can boost the overall security posture of your internal network. If a machine on your network does become compromised, you have assurance that the adversary won’t make it very far. Lastly, Managed Event Collection & Correlation gives you 24×7 monitoring from advanced log analysis tools and nGuard professionals who are trained to detect suspicious activity.